Integrate your Lucid Enterprise account with an identity provider (IdP) to enable your users to authenticate using SAML single sign-on (SSO) through your IdP. The purpose of this post is to provide instructions on how to configure unofficially supported IdPs to work with Lucid via SAML.
Before you configure Lucid with an IdP you will need to follow these SAML authentication steps in Lucid:
- Select Admin.
- Click Security in the left-hand menu.
- From the dropdown, select Authentication.
- Select Configure to the right of the “Allow SAML authentication” option to navigate to your SAML Activation page in Lucid. You will not be able to enable SAML until you have populated your domain and uploaded metadata.
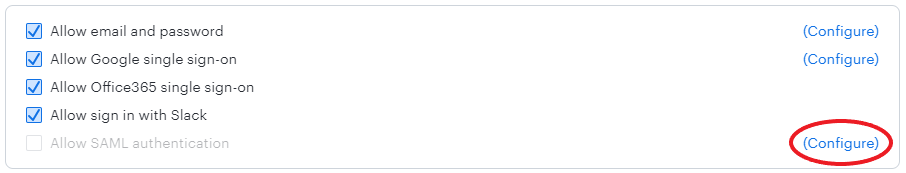
- Under "Lucidchart Sign in URL," enter your Domain name.
- Ensure the domain you are using is not already in use, which will cause the XML file to not upload properly.
- Ensure the domain you are using is not already in use, which will cause the XML file to not upload properly.
- Click Save Changes.
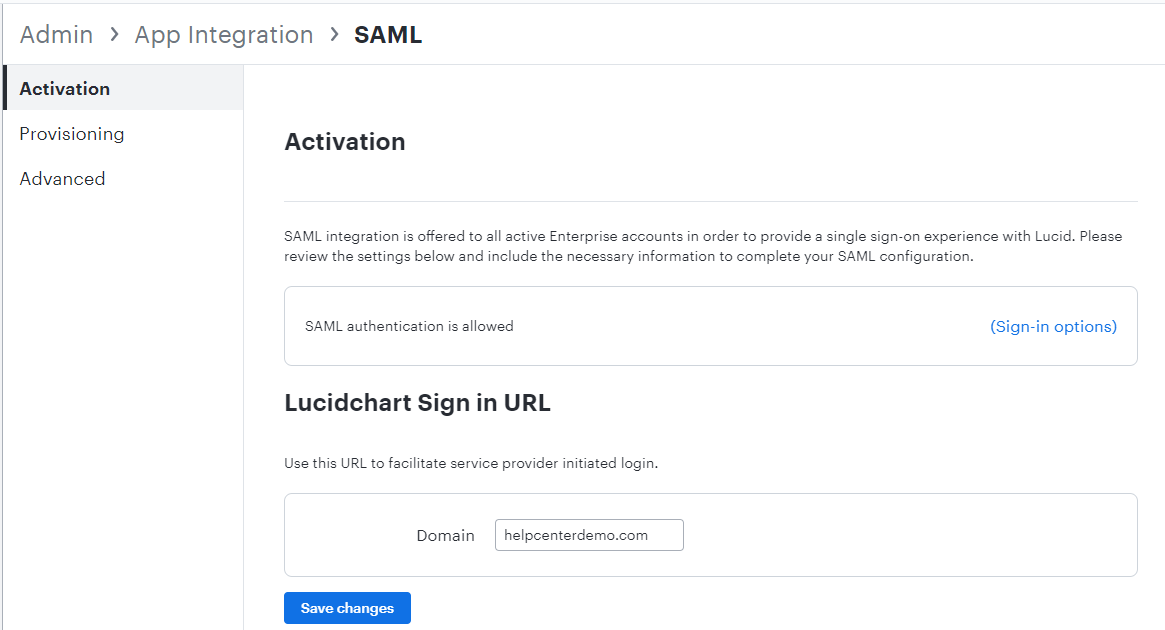
- Scroll down on the SAML Activation page of Lucid and click Add Identity Provider to upload the XML file you downloaded from your IDP.
- The metadata will populate the following fields:
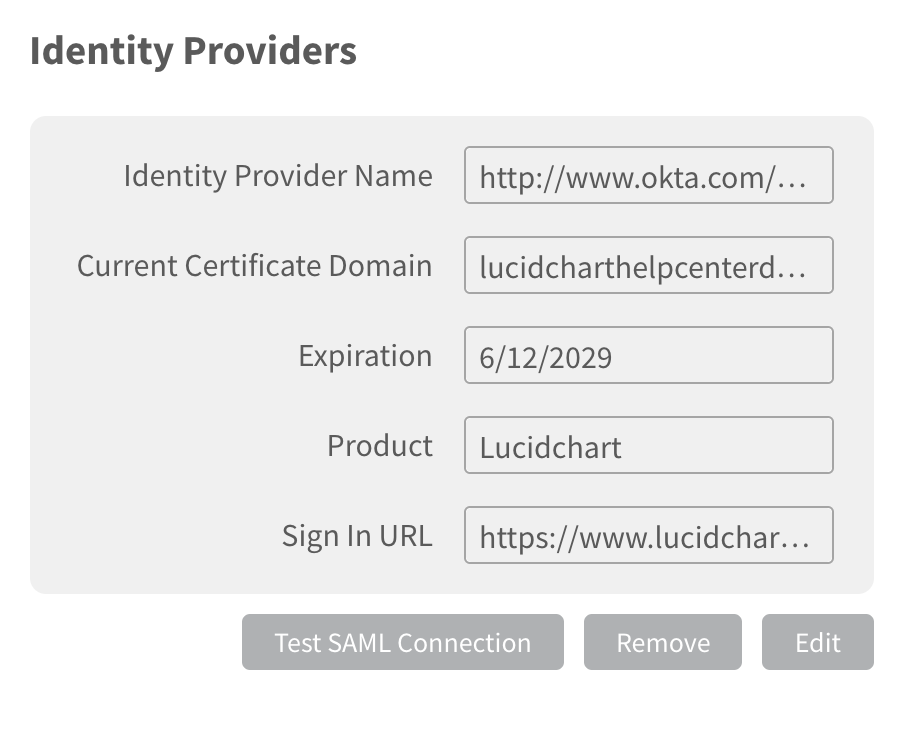
- The metadata will populate the following fields:
- Click Test SAML Connection to verify that Lucid is properly communicating with Okta.
- The connection will only work if the Lucid app has been assigned to your test user in Okta. You can assign the app to users in the Assignments section of the app page.
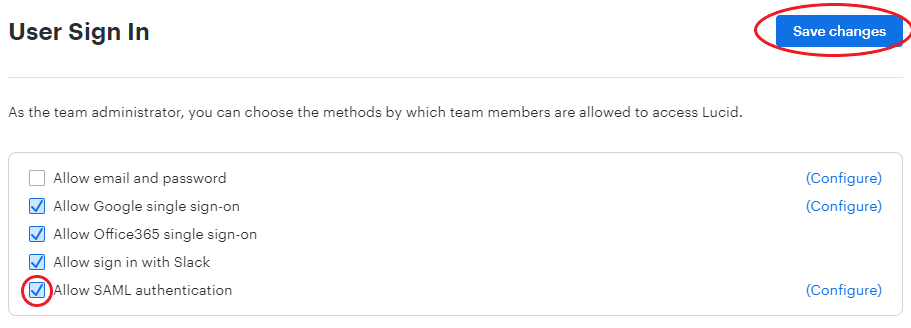
- Navigate back to the Authentication page.
- Check the box next to "Allow SAML authentication".
- Click Save changes.
To download the XML file and complete the configuration steps in Lucid, please review the post for your IdP below:
- Google SAML Configuration Guide
- JumpCloud SAML Configuration Guide
- Ping Identity SAML Configuration Guide
Google, JumpCloud, and Ping Identity are not officially supported IdPs, so you may notice that the instructions or screenshots in these posts may become outdated over time.
Testing your SAML Connection
After you have completed the configuration steps in Lucid and in your IdP, click on Test SAML Connection to ensure the configuration is correct. If the test says OK, then SAML has been configured correctly.
