Hello,
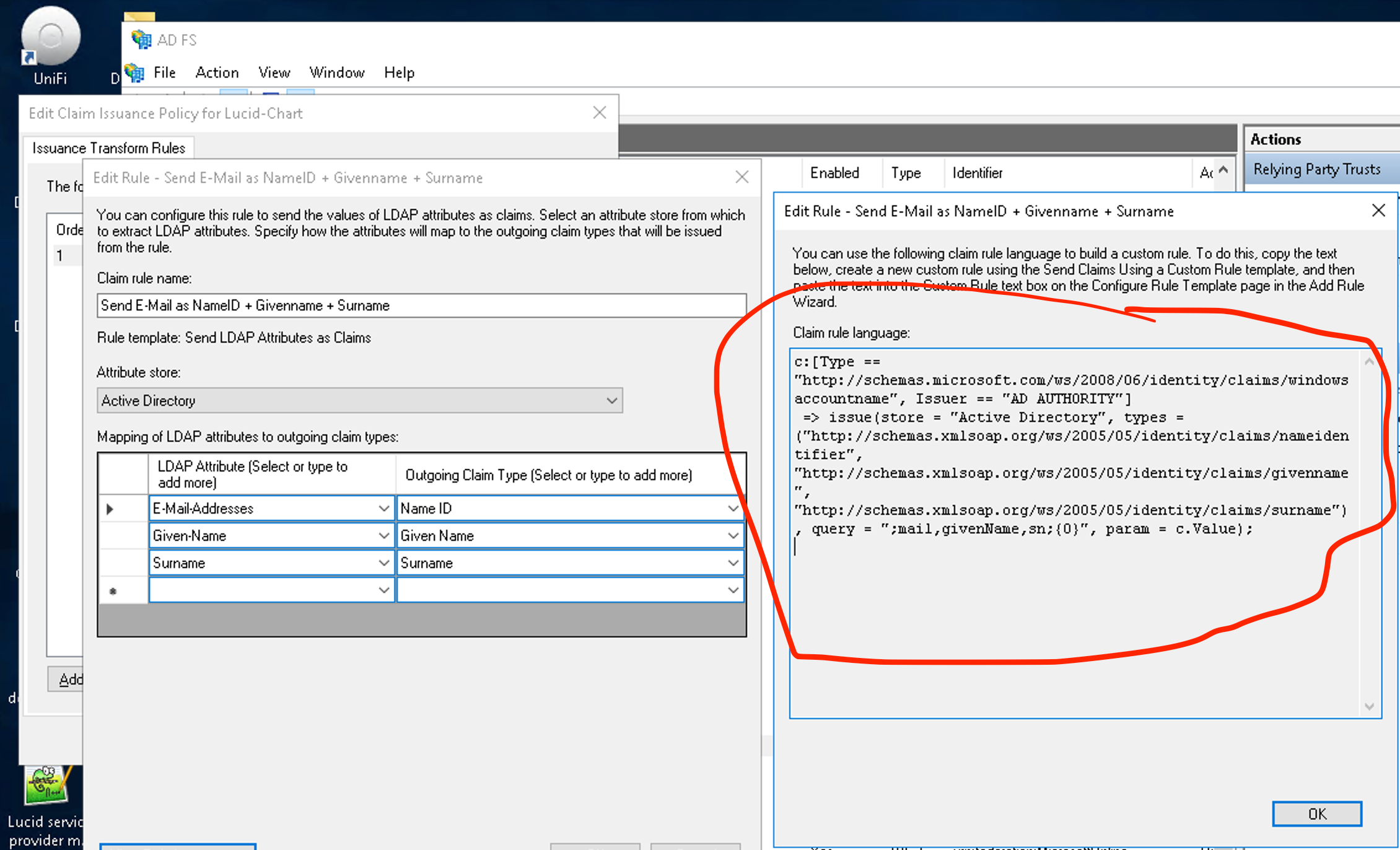
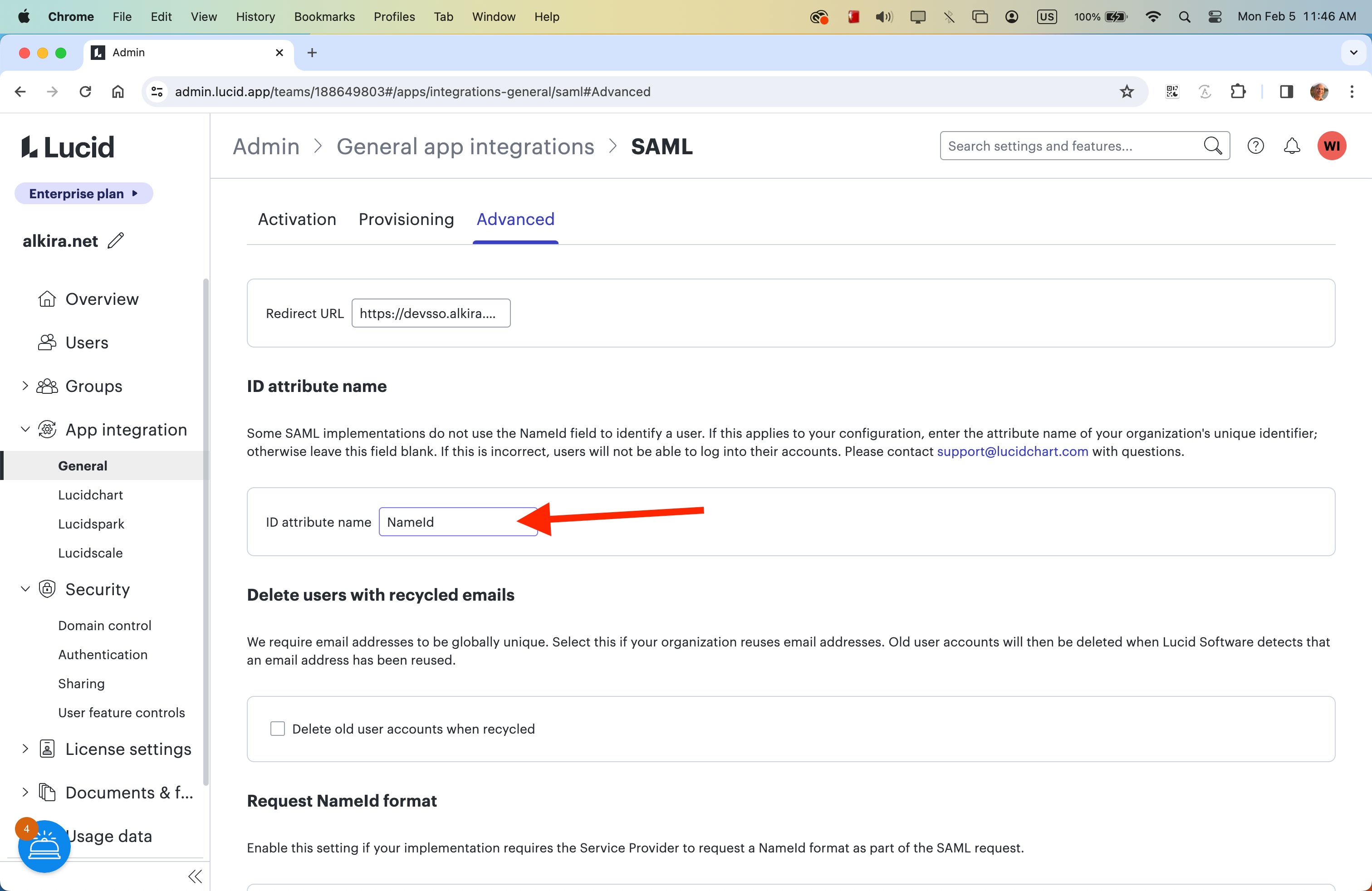
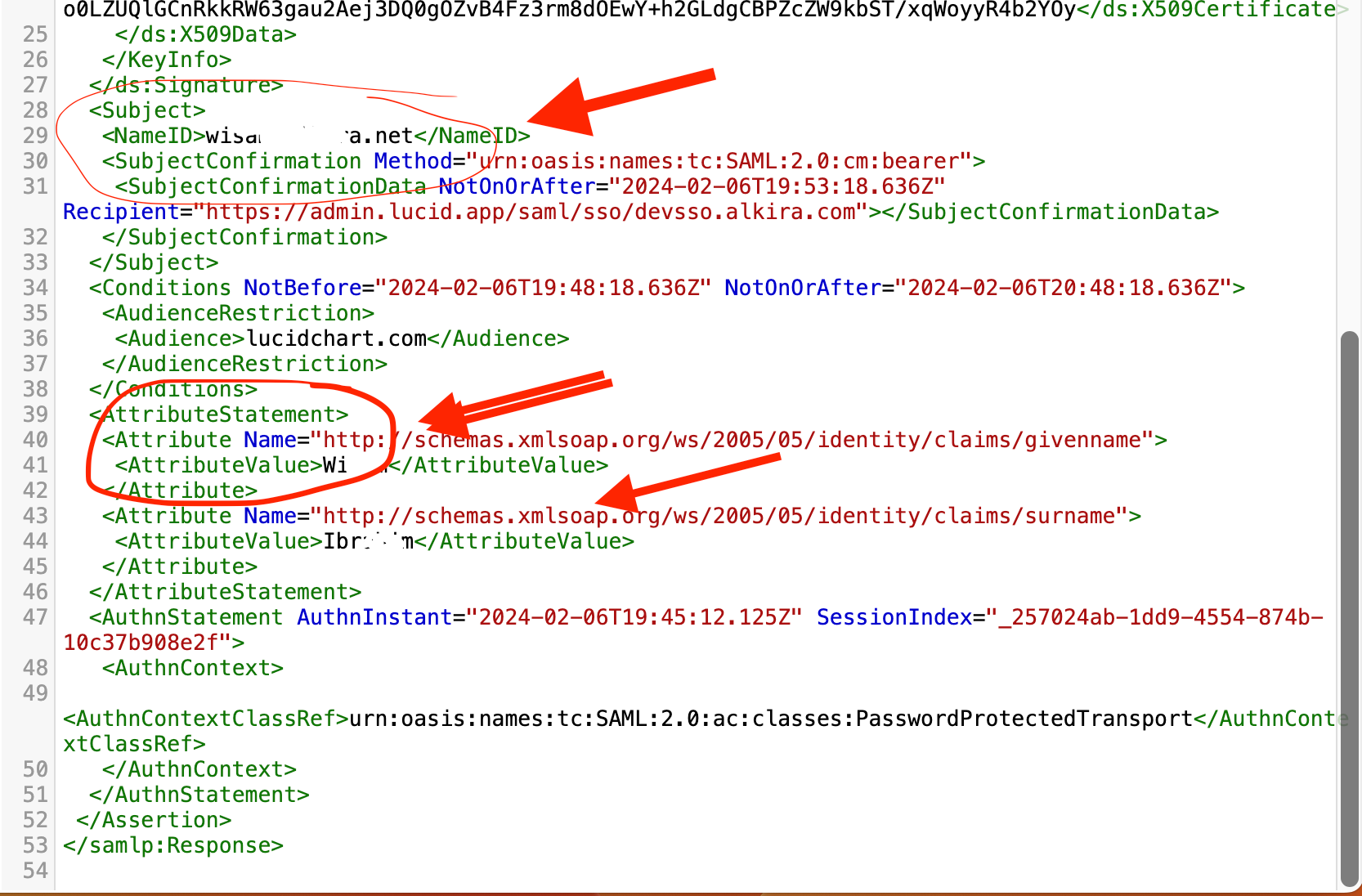
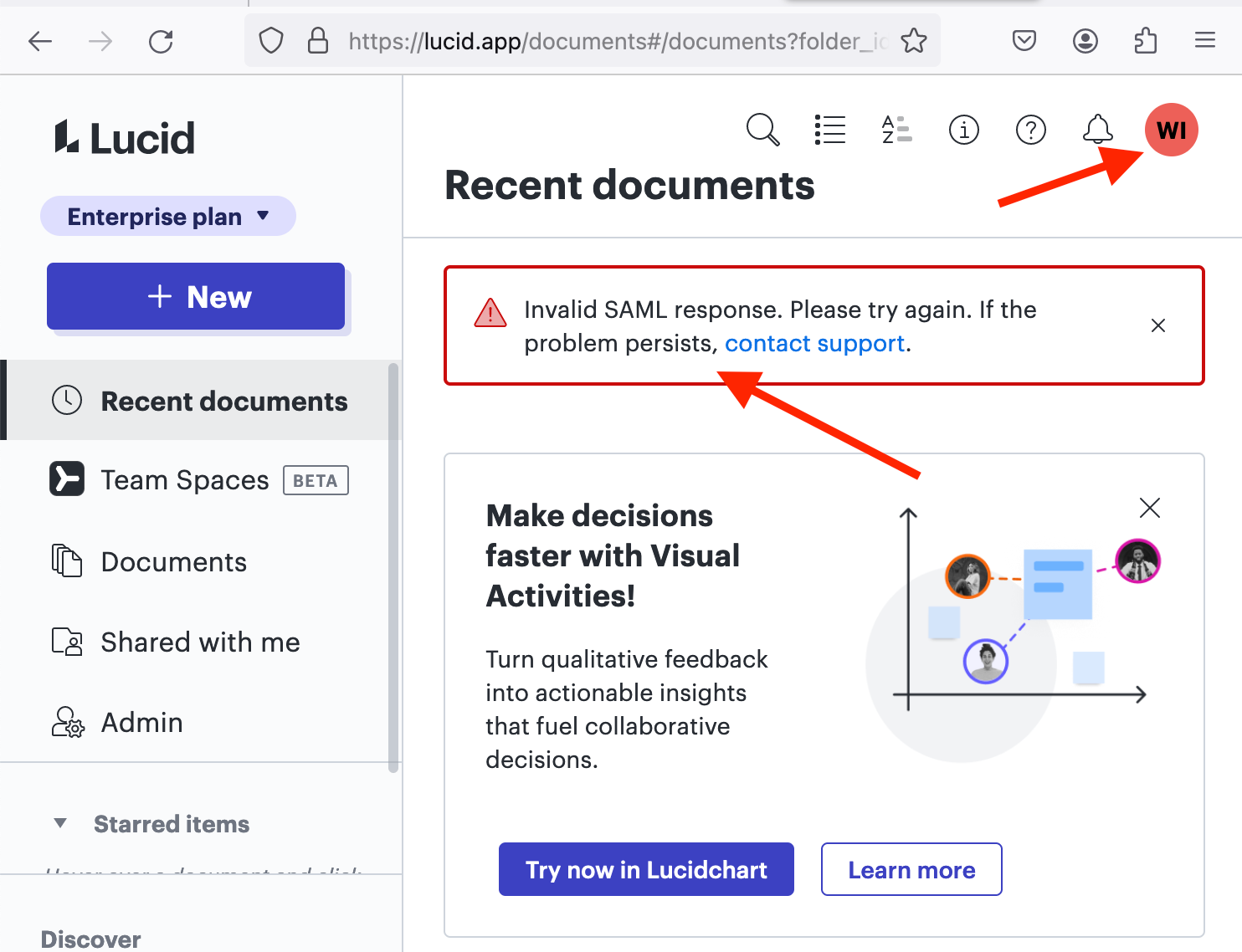
I'm getting this error when trying to set up my ADFS as IDP “SAML response missing required custom identifier.”. I followed the step-by-step instructions from the support website on:
There seem to be having some conflicting information between the instructions and what I receive in the meta-data file what I imported to my adfs. Is the above document up-to-date?
Best answer by Leianne C
View original