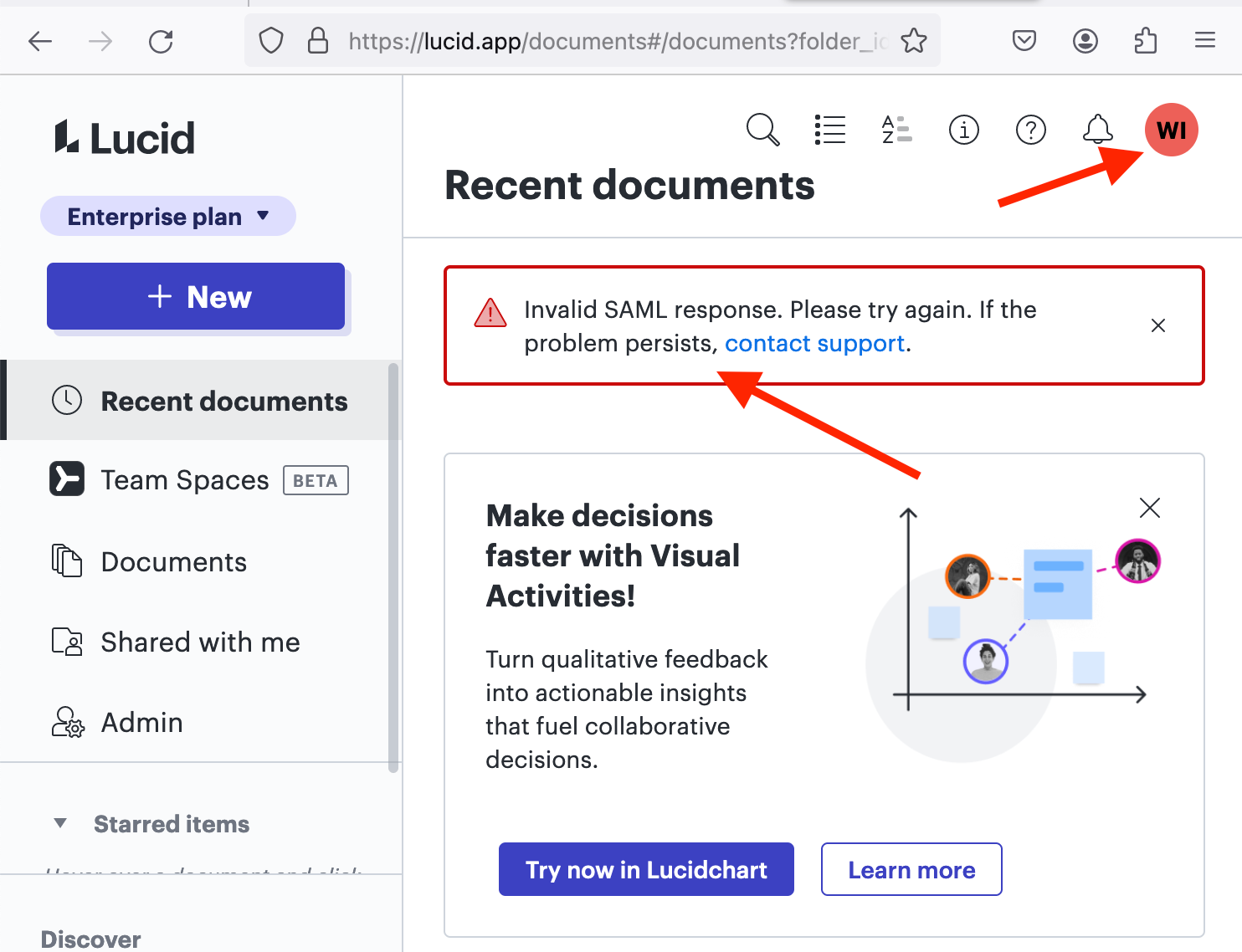
Hi @ak-wisam, thank you for following up and sorry for the delay as I checked with our internal teams for addition insight!
I can see that you have also submitted a support ticket for this issue and it has been transferred to the correct team. Someone should reach out to you shortly to further assist.
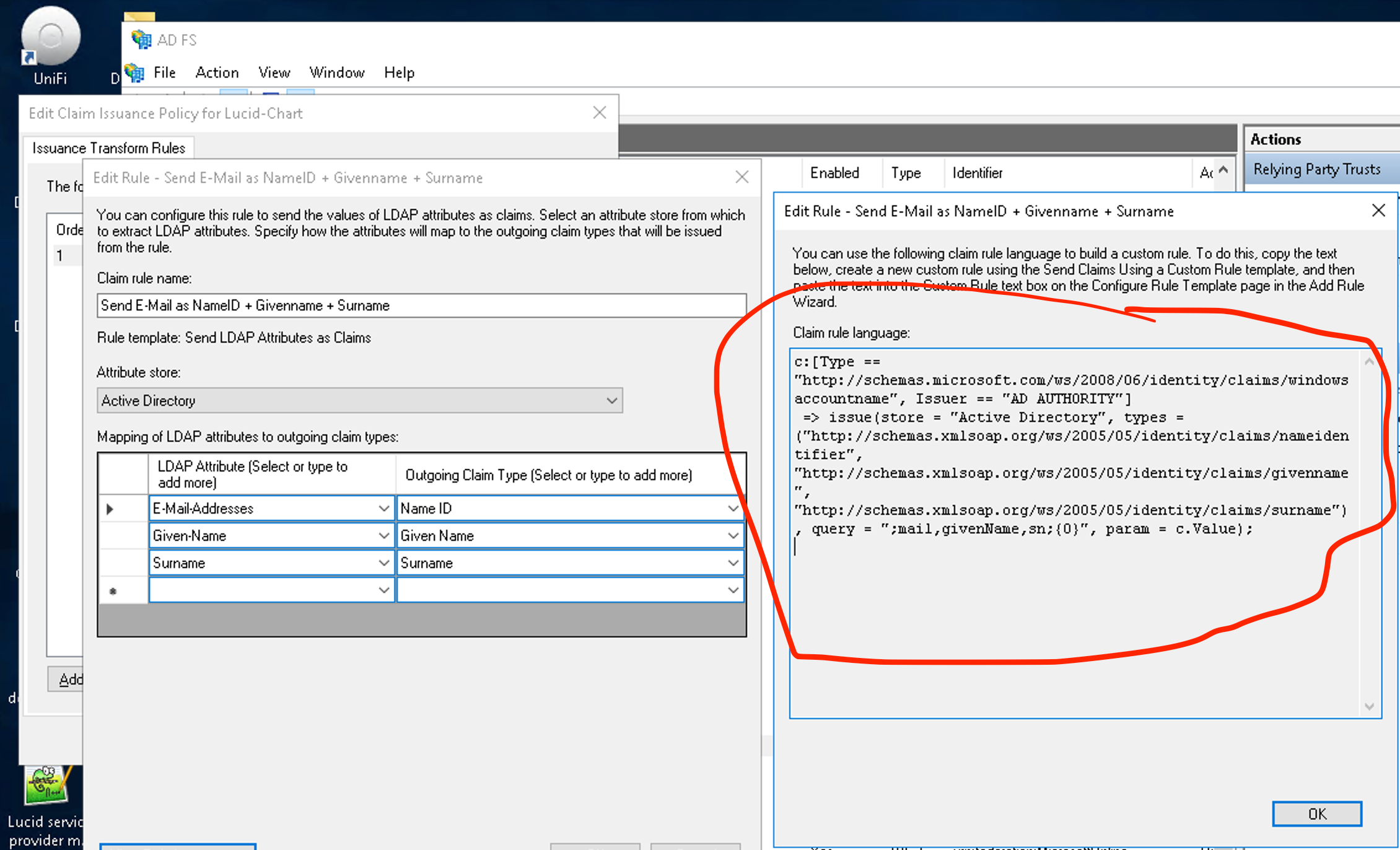
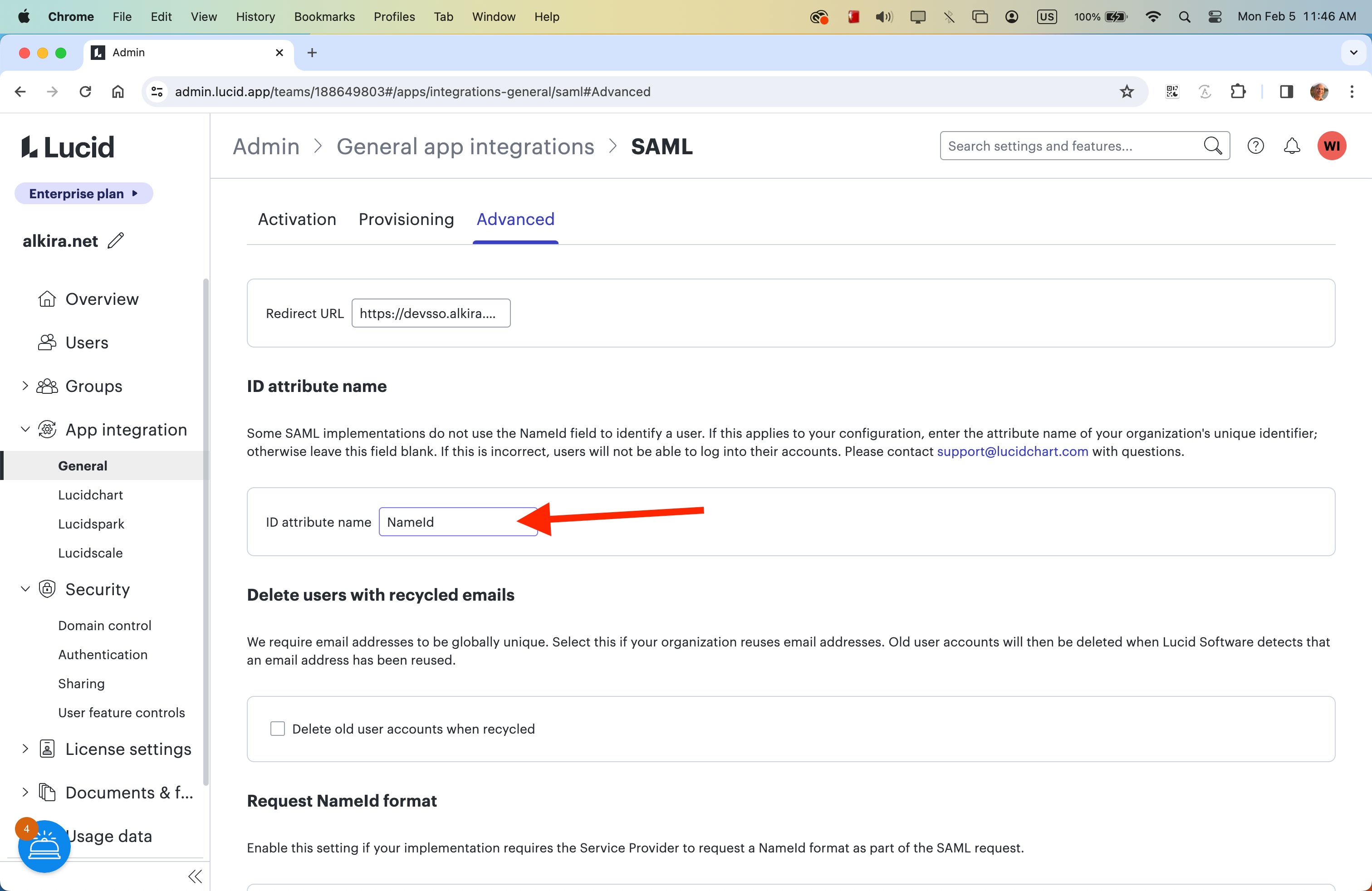
In the meantime to help troubleshoot, could you please also try removing the ‘NameID’ that you’ve added to the ‘ID Attribute Name’ field in advanced - leaving this field blank?
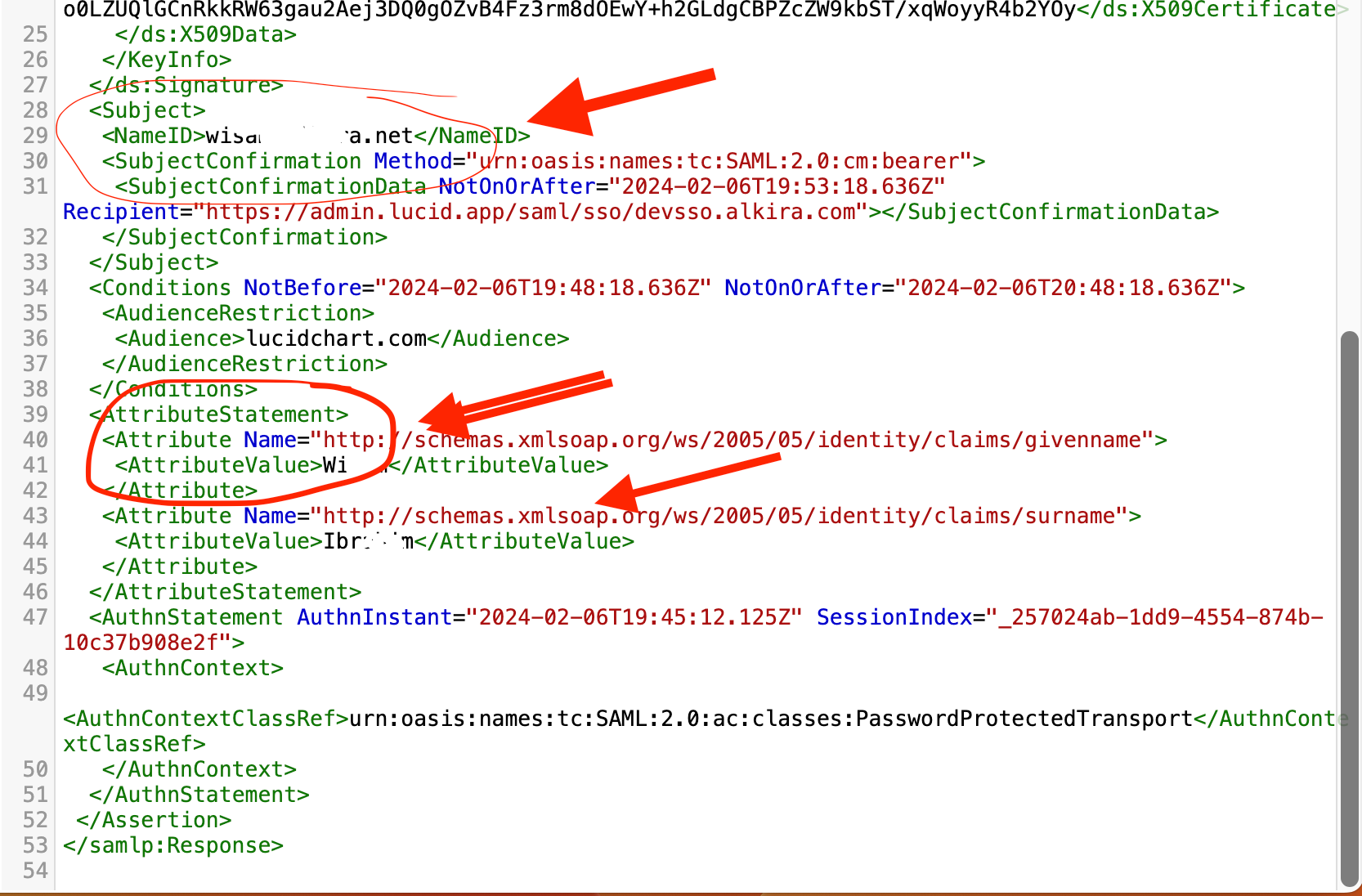
Regarding the attribute statement we are expecting, I would recommend checking this SAML Overview article for some additional information.
Hope this helps! Please let me know if you see any changes after trying the above step, or if you have any additional questions. Thank you!