Hi there. I have been successful in configuring SAML SSO with our Azure Entra ID tenant and our Lucid Enterprise tenant. Lucid's auto-provisioning accounts from SSO does indeed create the Lucid account but there is one issue I am hoping someone can help fix.
When the auto-provisioning happens upon first SSO login, the First Name and Last Name do not get filled in properly from their Azure Entra ID account. The First name gets the part of their email address before the @ sign and the Last name is blank.
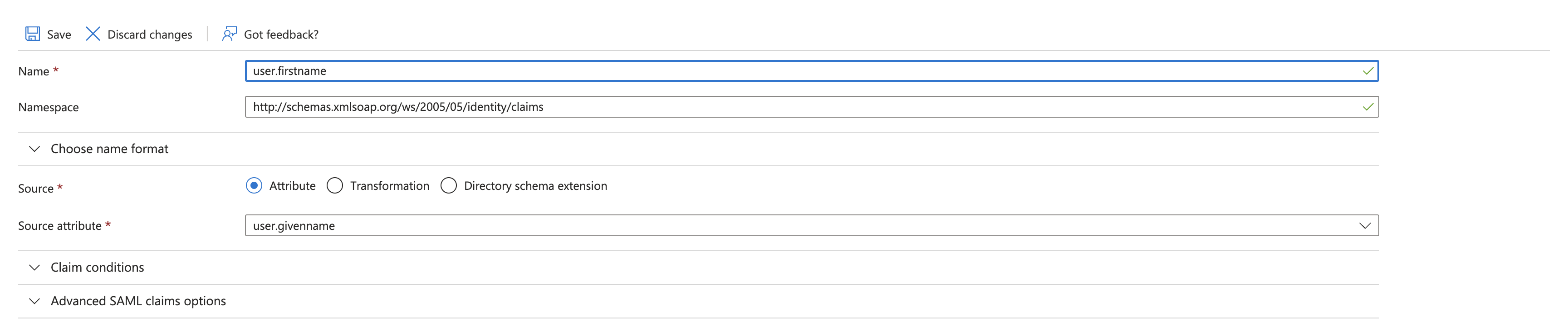
I searched for an read Lucid documents/tips on configuring SAML SSO as well as ones which indicate the SAML attribute statement mappings. However, Azure Entra ID does not have the same attribute names. For First name Azure has user.givenname; for Last name Azure has user.surname.
Is this something that can be corrected by modifying the standard attributes/claims for the Lucid (All products) SAML app? Here is what comes standard in Azure Enterprise Applications for Lucid (All products):
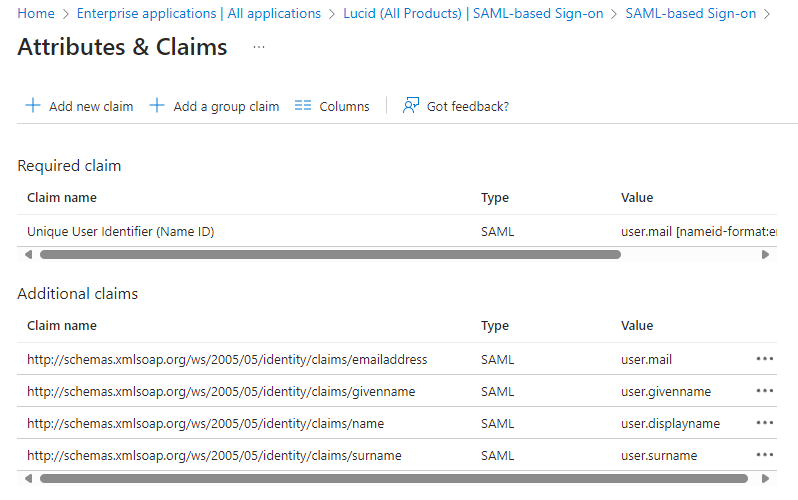
SAML Attribute statement mappings:
| Value Name | Accepted naming convention | OID naming convention |
| user.email | urn:oid:0.9.2342.19200300.100.1.3 | |
| first name | user.firstname | urn:oid:2.5.4.42 |
| last name | user.lastname | urn:oid:2.5.4.4 |